Request & Share Sensitive Client Data, Securely
No more insecure emails, scattered passwords, or manual follow-ups – just a seamless, secure, and trusted process.
Request Accessno credit card required
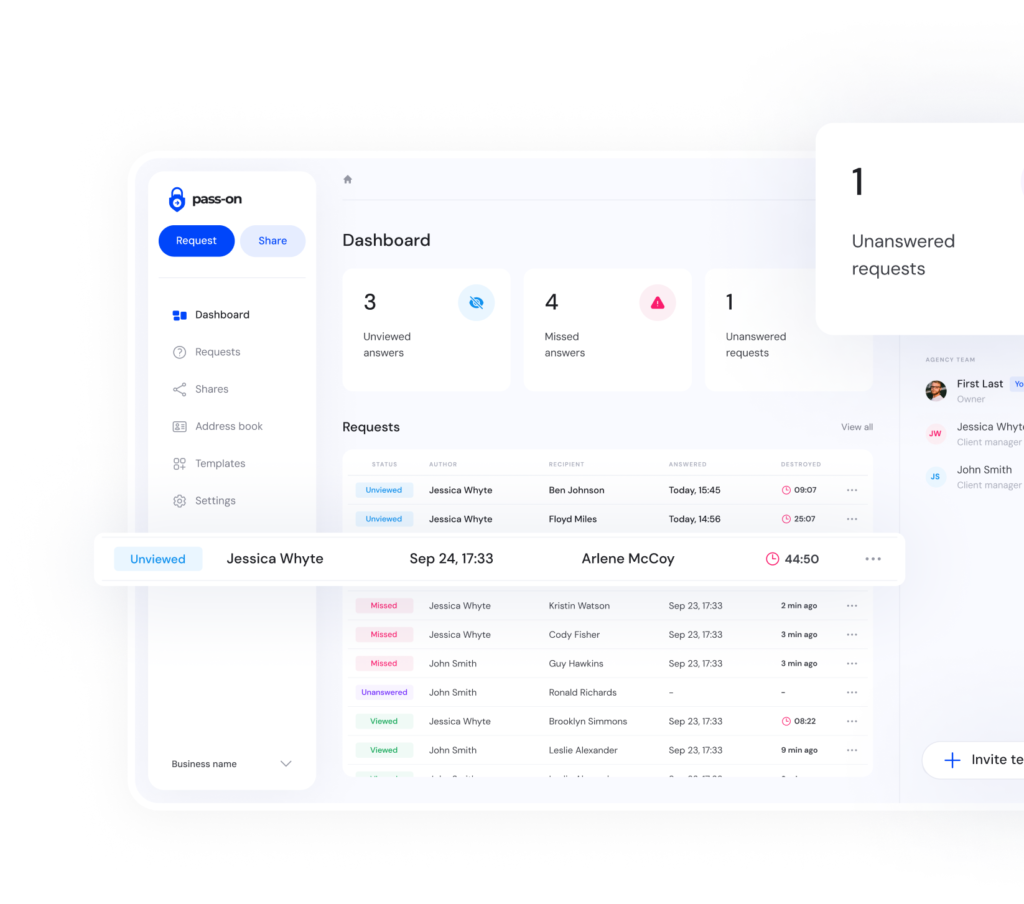
Stop Wasting Time Chasing & Sharing Sensitive Client Data
The Problem
A Messy, Insecure Process
Requesting and receiving sensitive client information can be a frustrating and risky process:
- Passwords and login details are shared via email, chat, or documents—making them vulnerable to breaches.
- Chasing clients for access details wastes valuable time and slows down projects.
- There’s no secure, structured way to request, track, or manage sensitive data.
- Clients hesitate to share credentials, affecting trust and professionalism.
The Solution
A Secure, Effortless Workflow
With Pass On, securely collecting and managing sensitive client information is simple, professional, and automated.
- Structured requests let you collect exactly what you need—fast.
- Encrypted, one-time access ensures information is securely shared and automatically deleted.
- No client accounts required—clients can submit details in seconds.
- Branded requests reinforce professionalism and build trust with clients.
No more email chains. No more security risks. Just seamless, secure data exchange.
How Pass On Works
It’s fast, seamless, and built for IT professionals and agencies that take security and professionalism seriously.
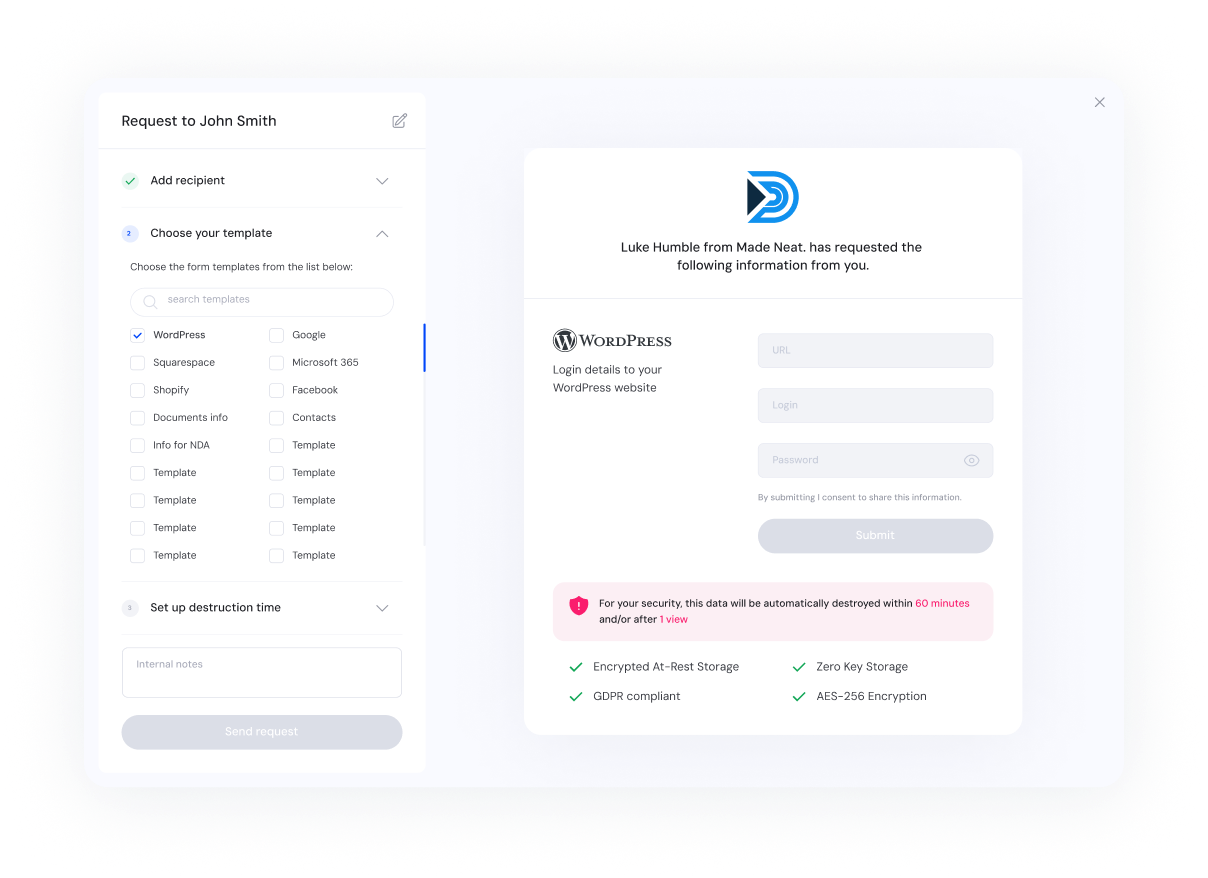
1. Request Securely
Effortlessly create structured data requests with predefined templates.
Simply select what you need, add a recipient, and let Pass On handle the rest.
2. Receive & Store Securely
Clients submit sensitive data through a simple, secure link – no accounts needed.
Everything is encrypted and stored safely until it’s accessed.
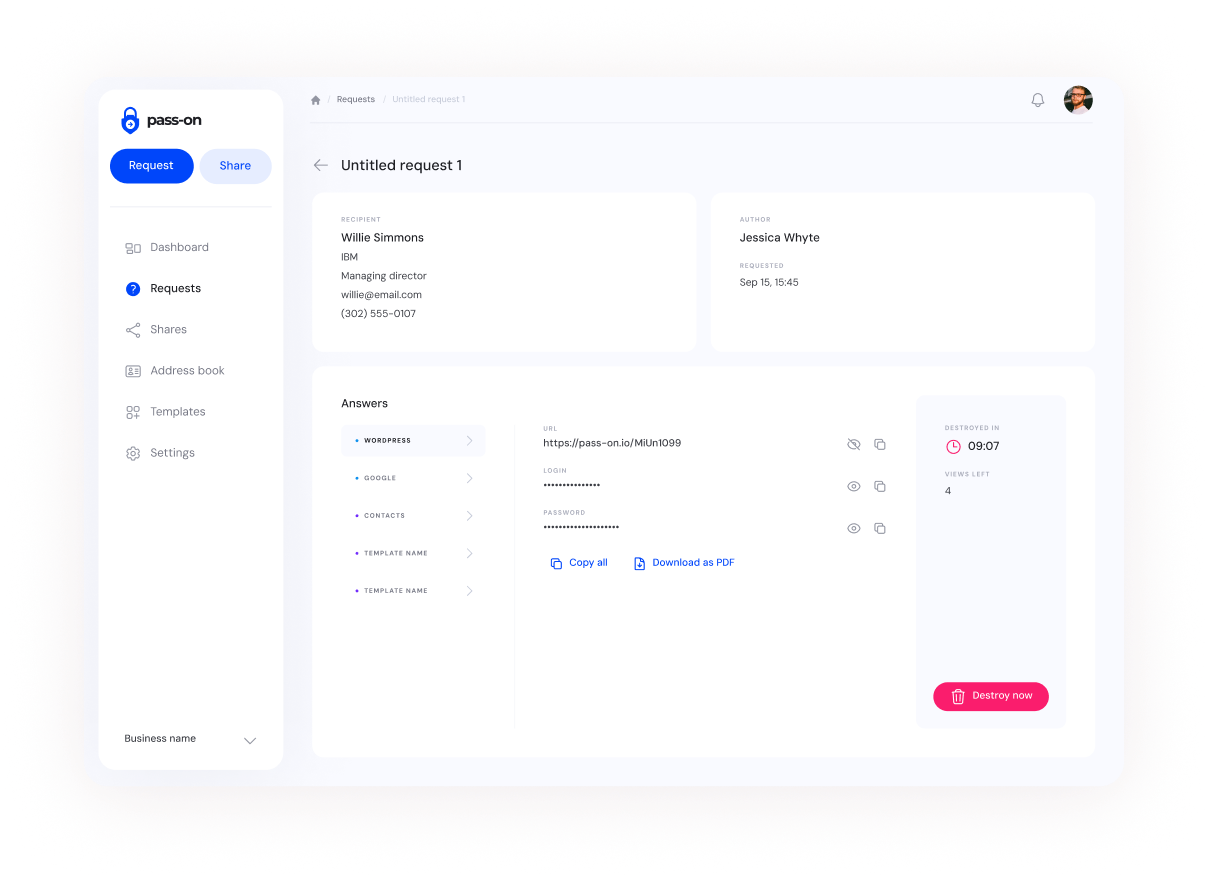
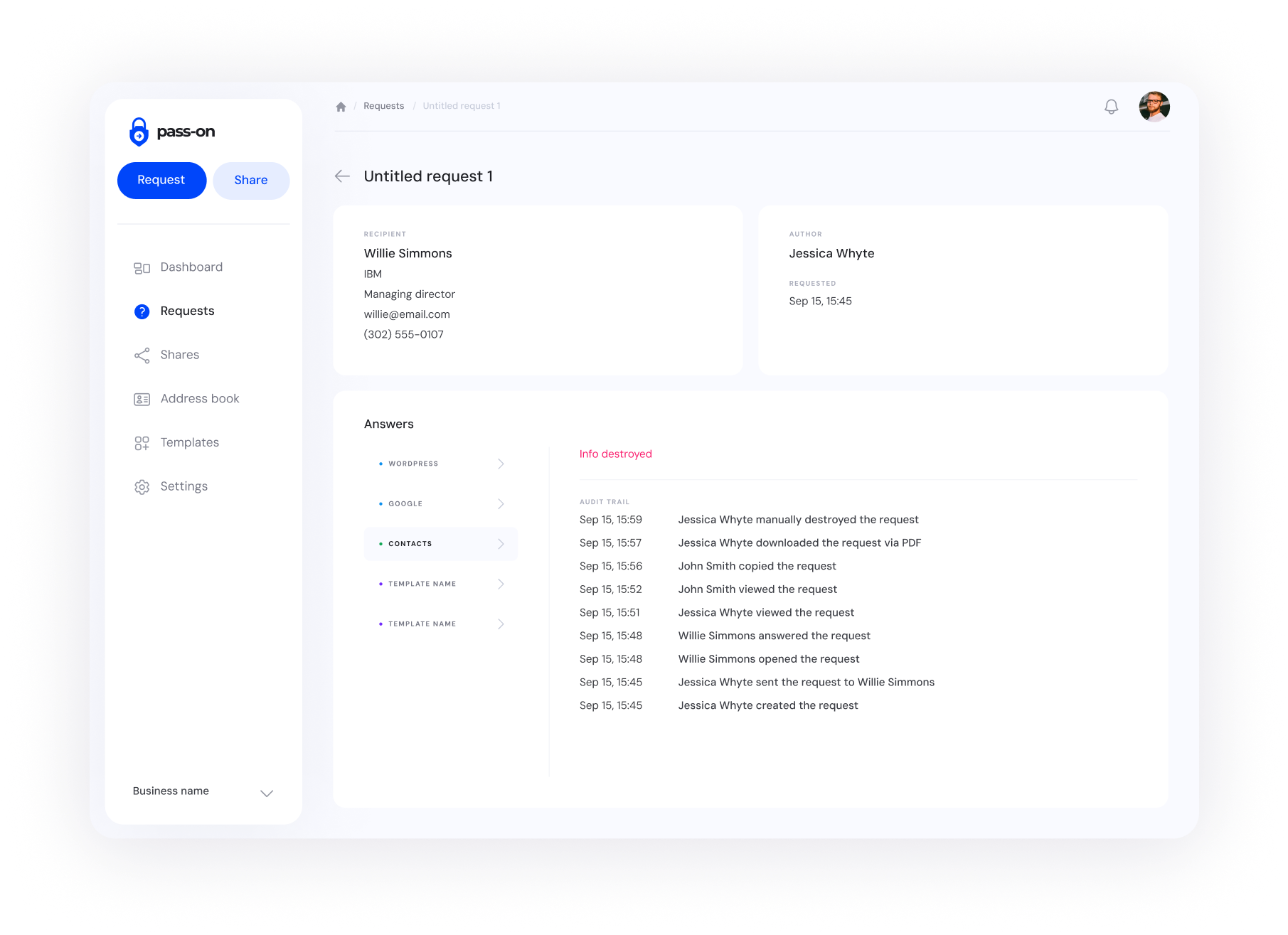
3. Automatic Data Destruction
Once the information is viewed, it is permanently deleted.
No more lingering passwords or forgotten access details posing a security risk.
Why IT Professionals & Agencies Choose Pass On
Pass On isn’t just about security – it’s about making
your workflow smooth, fast, and worry-free.
Trusted by People Who Care About Security
- All data is encrypted in transit and at rest, ensuring no unauthorized access.
- Information automatically deletes after access or a set expiration time.
- Meets strict data privacy regulations to protect your business and clients.
Simplifies Workflows & Saves Time
- Pre-built & custom templates help you request common information quickly.
- Automated reminders keep clients on track without the back-and-forth.
- History log lets you track requests without storing sensitive data.
Strengthens Client Trust & Reputation
- Custom branding lets you add your logo and colors for a seamless client experience.
- Professional, secure data collection shows clients you take their security seriously.
- No client accounts required – they submit information in just one step.